Background

Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network, like the internet. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users’ identities.
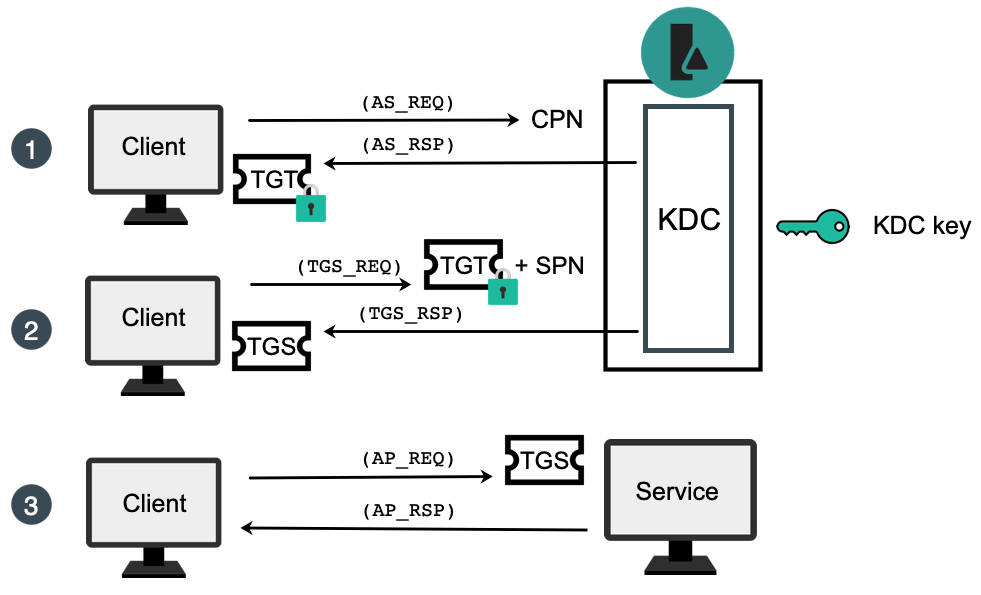
Since Windows 2000, Microsoft has used the Kerberos protocol as the default authentication method in Windows, and it is an integral part of the Windows Active Directory (AD) service.
LDAP is commonly used to do authentication and authorization.
Windows ADDS uses LDAP protocol, but normally the enterprise ADDS will use Kerberos as authentication method, instead of simple bind.
How to access ADDS/Kerberos from OpenResty/Nginx?
As known, OpenResty does not have a fully functional LDAP library.
Let’s have a look at the current alternatives:
- lualdap
- No SASL auth, simple bind only
- Not based on cosocket, i.e. not async
- lua-resty-ldap
- No SASL auth, simple bind only
What about other programming lanuages?
- go-ldap
- rust-ldap3
- depends on
kinitto get service ticket first - no keytab, no ad-hoc credential support
- depends on
- python-ldap
- depends on
kinitto get service ticket first - no keytab, no ad-hoc credential support
- not async
- depends on
After investigation, I think bonsai is the best choice, which is a popular and active python ldap client library.
Highlights:
- asyncio support
- Full SASL support
- DIGEST-MD5 and NTLM
- GSSAPI and GSS-SPNEGO (keytab, ad-hoc credential support)
- EXTERNAL
- simple pythonic design
- based on robust and time-tested C libraries, e.g. libldap2, libsasl2, libkrb5
Why not encapsulate it so that we could reuse it in openresty?
lua-resty-ffi provides an efficient and generic API to do hybrid programming in openresty with mainstream languages (Go, Python, Java, Rust, Nodejs).
lua-resty-ffi-ldap = lua-resty-ffi + bonsai
Check this repo for source code:
https://github.com/kingluo/lua-resty-ffi-ldap
Demo
Set up a minimal ADDS
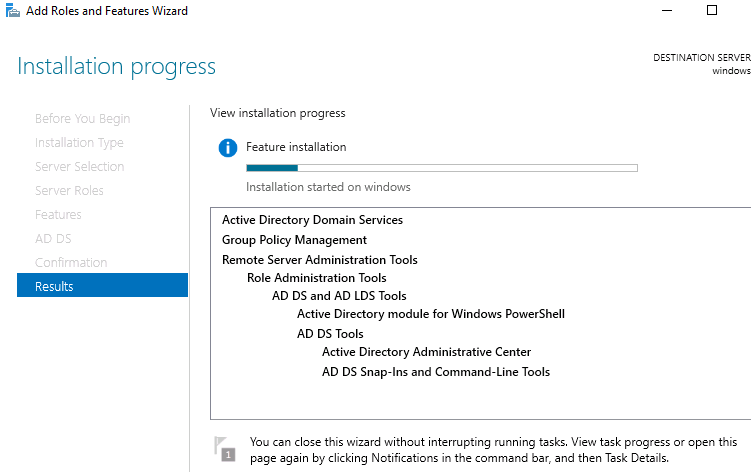
Let’s install a Windows ADDS on Window Server 2022 in VM.
From the server manager, add ADDS feature:
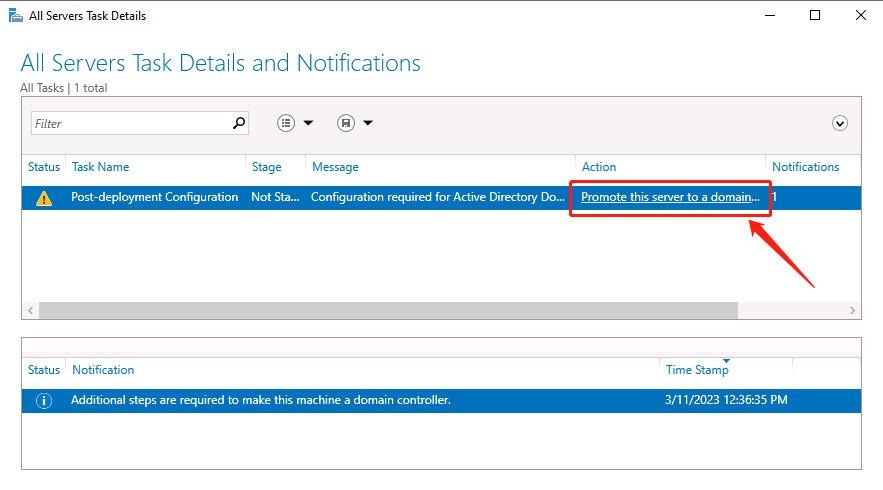
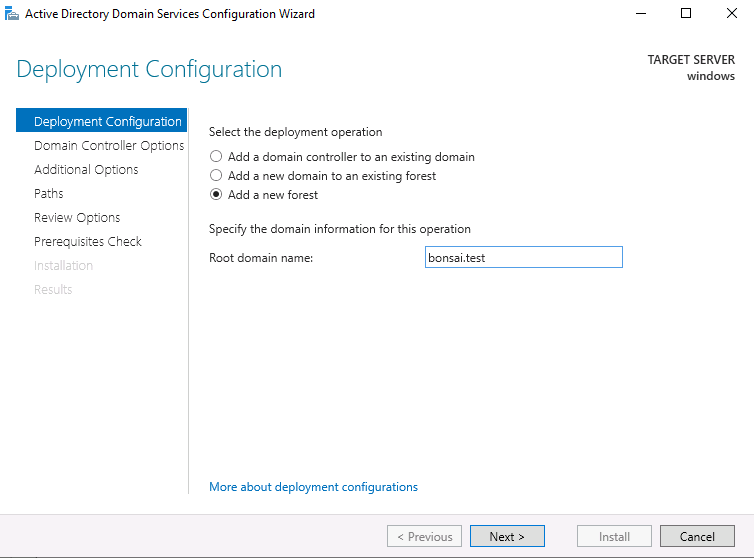
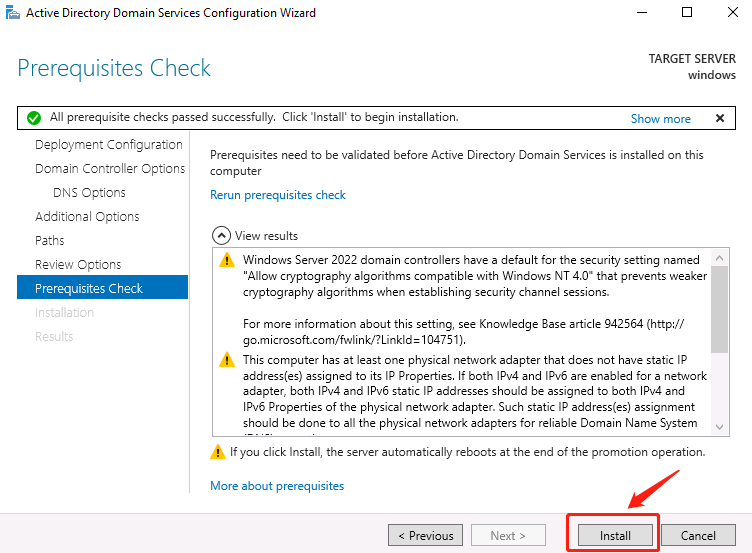
Promote this server to a domain controller:

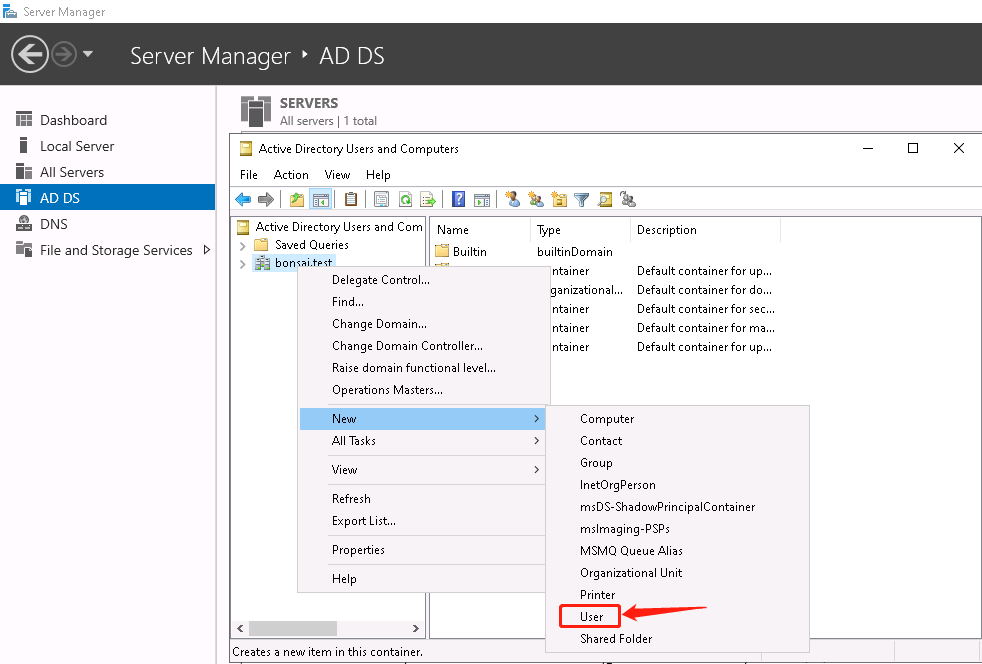
Add a user chuck:
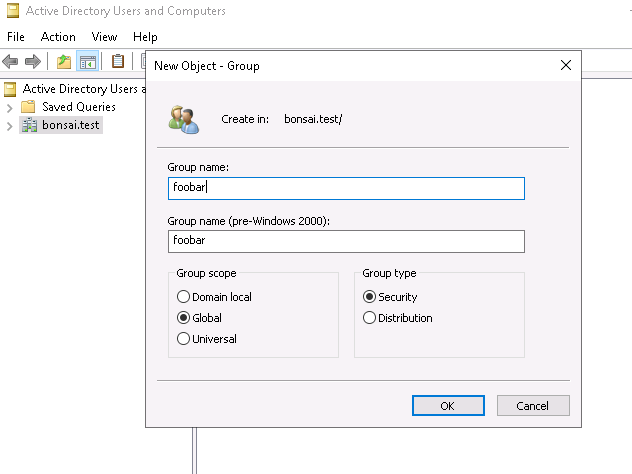
Add a group foobar:
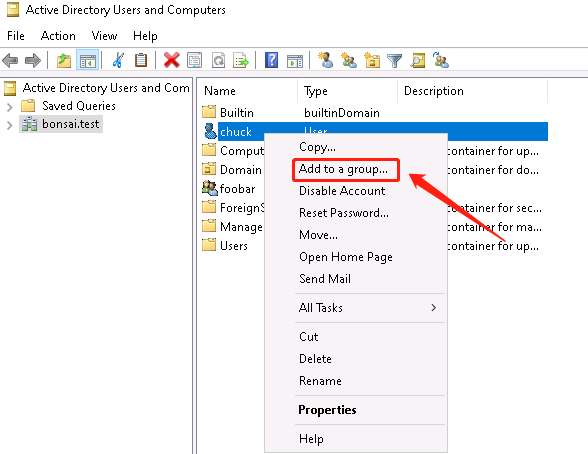
Attach user chuck to group foobar:
Done!
Use lua-resty-ffi-ldap
Add Windows IP into /etc/hosts:
# Hostname is windows
# Domain is bonsai.test
# IP is local network IP 172.30.90.18
172.30.90.18 windows.bonsai.test bonsai.test
Edit krb5.conf:
|
|
demo.lua
|
|
nginx.conf
daemon off;
error_log /dev/stderr info;
worker_processes auto;
env LD_LIBRARY_PATH;
env PYTHONPATH;
env KRB5_CONFIG;
events {}
http {
lua_package_path '/opt/lua-resty-ffi-ldap/demo/?.lua;/opt/lua-resty-ffi-ldap/lua/?.lua;/opt/lua-resty-ffi-ldap/lua/?/init.lua;;';
server {
listen 20000;
location /demo {
content_by_lua_block {
require("demo")()
}
}
}
}
Test:
|
|
Search result in JSON:
|
|
Conclusion
With lua-resty-ffi, you could use your favorite mainstream programming language, e.g. Go, Java, Python, Rust, or Node.js, to do development in Openresty/Nginx, so that you could enjoy their rich ecosystem directly.
Welcome to discuss and like my github repo: